Android and iOS users can install custom keyboards on their device. Alternative keyboards may offer various features to enhance the user experience.
Forensic artefacts from a third party keyboard have potential to offer insightful evidence which may corroborate other activity on a device.
One such keyboard application is GBoard, from Google.
Yohesh Khatri (@SwiftForensics) has already provided some detailed research into the Gboard which is well worth reading. I don’t intend to reinvent the wheel here. I just have one thing to add… session data!
Where it’s at!
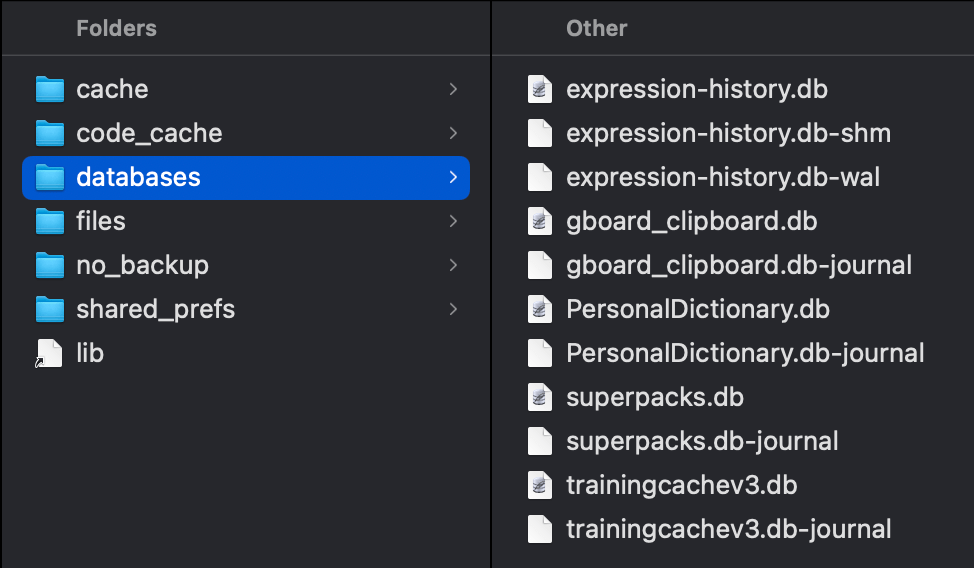
Data for the GBoard can be found at the below file path.
/data/data/com.google.android.inputmethod.latinThe databases folder on the test device I used contained the contents pictured below.
Session Data
Session data was found in the session table of the trainingcachev3.db database.
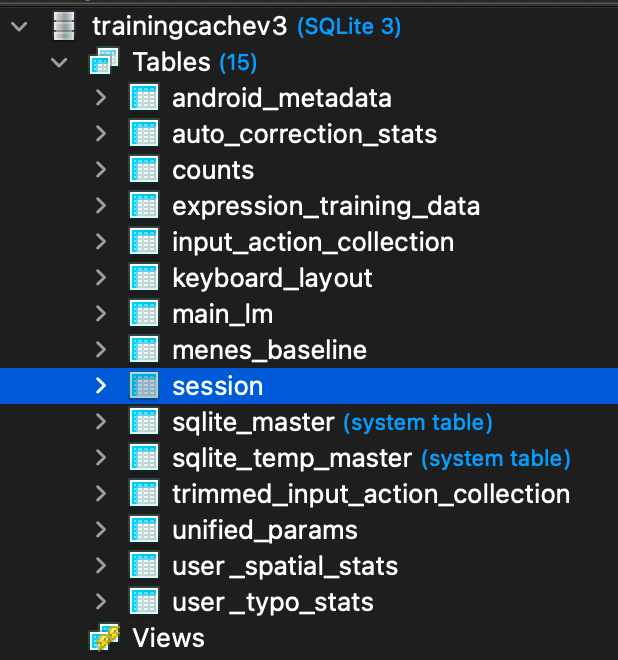
trainingcachev3.dbThe below video shows user activity on the test device, overlayed with the contents of the session table at the bottom right.
To get the session data, the below SQL was executed on trainingcachev3.db.
SELECT
session._session_id AS Session,
datetime(session._session_id / 1000, 'unixepoch') AS Start,
datetime(session._timestamp_ / 1000, 'unixepoch') AS Finish,
session.package_name AS Application
FROM
session


One response to “OMGboard”
[…] Kibaffo33OMGboard […]
LikeLike